CipherTrust Design and Implementation: A Complete Guide
CipherTrust Design and Implementation: A Complete Guide
Blog Article
Introduction to CipherTrust
CipherTrust, developed by Thales, is a comprehensive data security platform designed to protect sensitive data across on-premises, cloud, and hybrid environments. It provides robust encryption, centralized key management, and advanced access control to safeguard enterprise data while ensuring compliance with GDPR, HIPAA, PCI DSS, and other regulations.
A successful CipherTrust design and implementation ensures that organizations can securely manage encryption, protect critical assets, and enforce security policies without disrupting operations.
Key Components of CipherTrust
Before diving into the design and implementation process, it is essential to understand the core components of the CipherTrust Data Security Platform (CDSP):
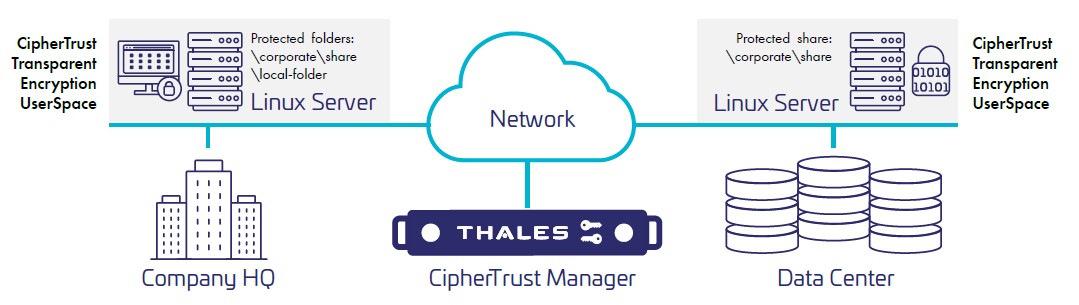
- CipherTrust Manager (CM) – The central console for managing encryption keys, policies, and access controls.
- CipherTrust Transparent Encryption (CTE) – Provides file- and folder-level encryption with policy-based access control.
- CipherTrust Cloud Key Manager (CCKM) – Centralizes key management for cloud providers like AWS, Azure, and Google Cloud.
- CipherTrust Application Data Protection (CADP) – Offers API-based encryption and tokenization for applications.
- CipherTrust Database Protection – Encrypts structured data in databases with minimal performance impact.
- CipherTrust Key Management – Manages encryption keys across multiple platforms, including HSMs (Hardware Security Modules).
CipherTrust Design and Implementation Strategy
1. Planning and Designing the CipherTrust Deployment
A well-structured CipherTrust deployment starts with careful planning.
Assess Business and Security Needs
- Identify sensitive data locations (on-prem, cloud, hybrid).
- Determine regulatory requirements (GDPR, HIPAA, PCI DSS, etc.).
- Define data security goals (encryption, access control, tokenization).
- Perform a risk assessment to evaluate potential vulnerabilities.
Infrastructure Considerations
- Choose between on-premises, cloud, or hybrid deployment models.
- Define network architecture, including firewalls, VPNs, and authentication mechanisms.
- Identify integration points with existing security solutions (SIEM, IAM, HSMs).
2. Deploying CipherTrust Manager (CM)
CipherTrust Manager is the foundation of the platform and must be deployed first.
Deployment Options:
- On-Premises: Deploy as a virtual appliance on VMware, Hyper-V, or KVM.
- Cloud: Available on AWS, Azure, and Google Cloud.
- Hardware Appliance: Install as a dedicated security appliance.
Installation and Configuration Steps:
- Deploy CipherTrust Manager and configure network settings.
- Set up role-based access control (RBAC) for administrators and users.
- Enable audit logging and integrate with SIEM solutions.
- Configure backup and disaster recovery policies.
3. Implementing Encryption and Key Management
Key Management Strategy:
- Generate, store, and manage encryption keys securely.
- Automate key rotation and expiration alerts.
- Enforce access control policies for key usage.
Integration with Cloud Providers:
- Connect CipherTrust Cloud Key Manager (CCKM) to AWS KMS, Azure Key Vault, or Google Cloud KMS.
- Implement Bring Your Own Key (BYOK) and Hold Your Own Key (HYOK) strategies.
4. Deploying CipherTrust Transparent Encryption (CTE)
CTE enables file-level encryption with granular access control.
Steps to Deploy CTE:
- Install the CTE agent on servers where data needs to be encrypted.
- Define encryption policies for files, folders, and applications.
- Set up granular access controls based on user roles and processes.
- Test policies to ensure only authorized users can access decrypted data.
5. Encrypting Databases and Applications
CipherTrust Database Protection:
- Encrypts sensitive data in Oracle, MySQL, SQL Server, PostgreSQL databases.
- Uses transparent encryption with minimal impact on database performance.
CipherTrust Application Data Protection (CADP):
- Encrypts application data using RESTful APIs and SDKs.
- Supports tokenization and format-preserving encryption (FPE) for data masking.
6. Monitoring and Compliance Enforcement
CipherTrust provides robust audit logging, monitoring, and compliance reporting.
Monitoring Tools:
- Enable real-time alerts for unauthorized access attempts.
- Integrate with SIEM platforms (Splunk, IBM QRadar, ArcSight).
- Generate audit reports for compliance verification.
7. Ongoing Maintenance and Optimization
Key Actions:
- Regular Software Updates – Keep CipherTrust software up to date.
- Policy Adjustments – Modify encryption policies based on evolving threats.
- User Access Reviews – Periodically review and refine access controls.
- Key Rotation and Backup – Automate key rotation and maintain secure backups.
Benefits of Implementing CipherTrust
✔ Centralized Data Protection – Secure on-premises, cloud, and hybrid environments.
✔ Regulatory Compliance – Align with GDPR, HIPAA, PCI DSS, and more.
✔ Seamless Integration – Works with HSMs, SIEM, IAM, and cloud platforms.
✔ Granular Access Controls – Prevent unauthorized access to sensitive data.
✔ Scalable Security – Future-proof encryption for expanding data needs.
Conclusion
A successful CipherTrust design and implementation ensures enterprise-wide data security, compliance, and encryption agility. By following best practices for deployment, encryption, access control, and monitoring, organizations can protect sensitive data from cyber threats, insider risks, and regulatory penalties.
CipherTrust is a future-proof solution that enables enterprises to manage encryption keys, secure applications, and enforce data protection policies—whether on-premises, in the cloud, or across hybrid environments. Report this page